Protecting Domain Windows PCs and Servers with SRP
Why use SRPs with the GPOs allowed with Active Directory?
Tranquil IT uses SRP at all its managed services clients to prevent the execution of any unknown software or executables.
Setting up this type of method requires a little time and listening, as the existing stock of unknown software and executables has to be cleaned up. Once SRP is well mastered, ransomware and other viruses can no longer be launched by users and you have a sure view of what is deployed on the machines in your park.
Legitimate enterprise software can then be deployed with the WAPT software deployment tool.
At Tranquil IT, we found that 2 SRP GPOs provided a good ratio between complexity and efficacy:
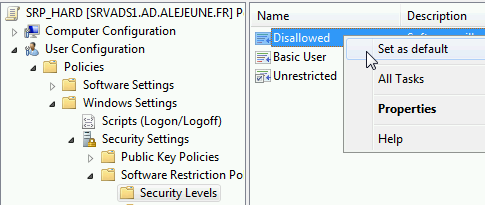
SRP_light: Blacklist mode to block unapproved applications, paths and extensions.
SRP_hard: White List mode to allow only approved applications, paths and extensions.
The strategy will be to first place your users in a SRP_light OU, then gradually switch them to a SRP_hard OU.
Implementing SRPs
Create the 2 UO SRP_light and SRP_hard.
SRP_light
Create the OU SRP_light:
Creating a new Organizational Unit
Name your Organizational Unit SRP_LIGHT:
Naming the Organizational Unit
Enable the User Restriction Policy GPO:
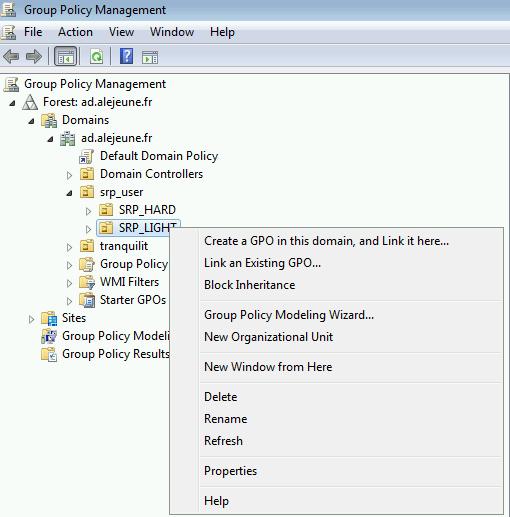
Creating the new GPO
Go to .
Then, :
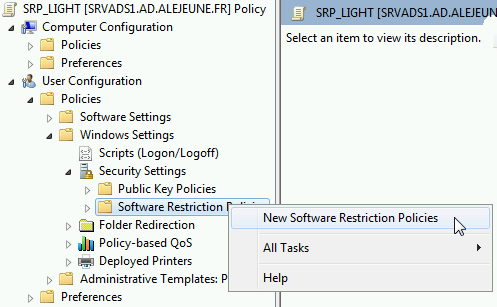
Creating the new SRP rule
In , leave the security level on Unrestricted:

Creating the new GPO
In , add restricted:
.js
%USERPROFILE%Download*
Example with .js, create a new path rule in
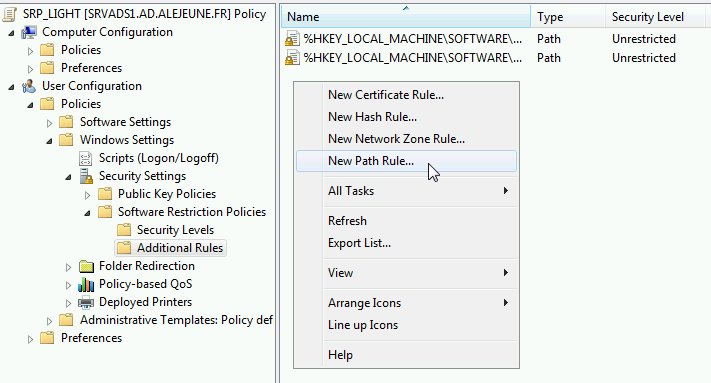
New path rule of the SRP GPO
The path accepts wildcards
*, it will be useful for .js extensions.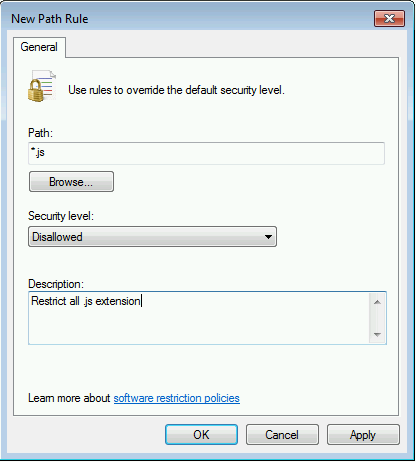
Option for the new .js path rule on the SRP GPO
It is also possible to use environment variables such as
%USERPROFILE%to apply a rule to all users.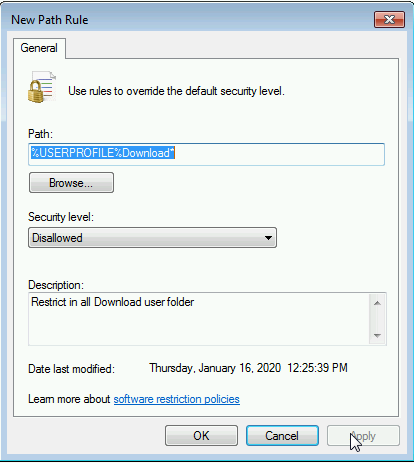
Option for the new rule applicable to user profiles on the SRP GPO
SRP_hard
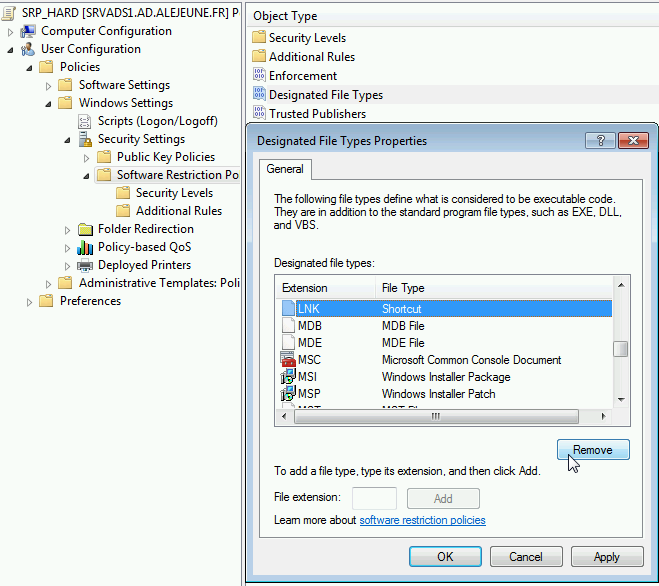
Software Restriction Strategies and File Types
Software Restriction Strategies and Additional Rules
For current and known directories, add these rules as unrestricted (Add any directory where authorized executables can be found):
%allusersprofile% %LOGONSERVER% %public% %tmp%\getpath.cmd \\ipsrvad \\srvads.domaine.local \\srvads \\applicationmetier
%HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ProgramW6432Dir% %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ProgramFilesDir (x86)%
For folders to be added in the forbidden list:
C:\Windows\Temp\*
For registry keys to be potentially restricted (do not apply for the moment):
%HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\Debug %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\PCHEALTH\ERRORREP %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\Registration %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\System32\catroot2 %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\System32\com\dmp %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\System32\FxsTmp %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\System32\spool\drivers\color %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\System32\spool\PRINTERS %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\System32\spool\SERVERS %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\System32\Tasks %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\SysWOW64\com\dmp %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\SysWOW64\FxsTmp %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\SysWOW64\Tasks %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\Tasks %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot%\tracing
Business software
Add to the unrestricted list the paths to the business software used in your Organization. The list below is provided as a EXAMPLE:
C:\AFICEGI C:\AFISRV C:\AFIWEB2 C:\Arpege C:\Carteplus C:\Cilw
Add to the unrestricted list the paths to the software you absolutely must use but which are extracted in
Local Settingsunder Windows XP, example with the LogMeIn applet:%userprofile%\Local Settings\Application Data\LogMeIn Rescue Applet\
Note
Whenever possible, it is preferable to use installers that extract the binaries into the intended system directories, such as
C:\Program Files(x86)\orC:\Program Files\.
Using hashing rules
It is possible to add file hashes for executables on a USB key for example:
Copy / paste the binary on a share.
Repatriate the binary onto the management machine.
Create a new hash rule:
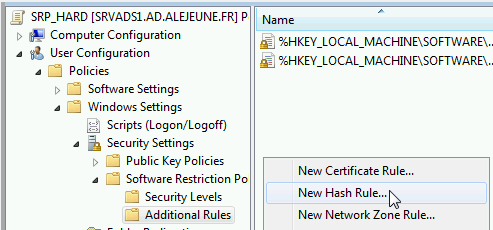
New hash rule
Select the binary file:

Fetching the binary file
The executable’s information will filled up automatically:
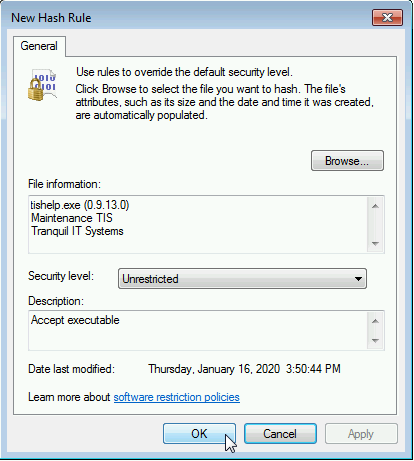
Hash added to the SRP rule
The new hash rule with the executable will appear in the list:
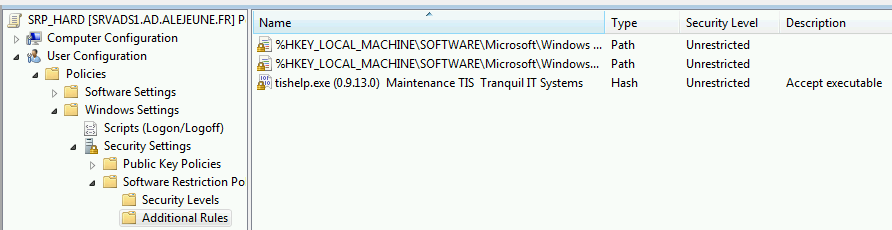
List of Hard SRP rules
Repeat until the executable starts properly (example TISHelp or Berger Levrault Payroll).
Using certificate rules
It is necessary to use a GPO rule to force certificate checking before running software (performance drop). This requires a preliminary testing phase on a staging Organizational Unit.
Go to and activate :
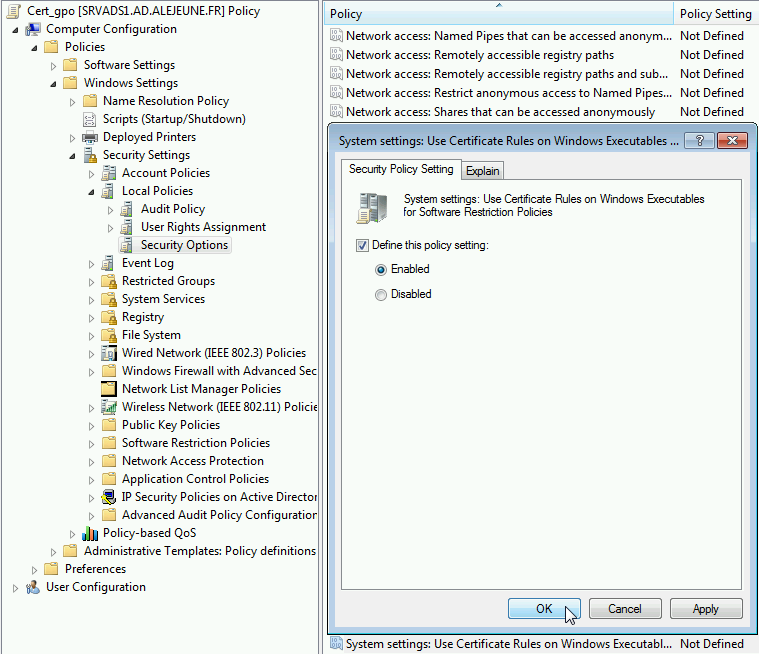
Enabling checks of certificates
Debugging procedure during lockups
Place all users in the SRP_light OU.
Place yourself with your restricted account in the SRP OU and launch all possible applications from all possible servers.
On Terminal Server environments, search for .exe in
C:Users.On the file server search for .exe in network shares.
Analyze in the eventvwr event viewer of each server or workstation the potentially blocked programs and add if needed the path in the additional rules.
Then move some voluntary users into the SRP_hard OU and let time do its work.
Depending on the problems and resolution methods you apply, move users step by step into SRP_hard:

Enabling checks of certificates
Iterating changes quickly
In case of blocked programs, there is no need to reboot the workstation, just run gpupdate /force in user context.
This allows you to reapply the new GPO settings without restarting the session.